In this article we will discuss in detail the vulnerabilities of symmetric cryptography.
MITM Attack:
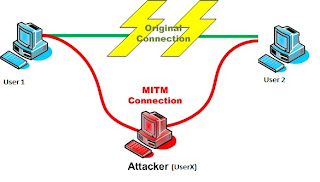
To understand the Man in the middle attack, let’s repeat the scenario where User1 & User2 wants to start encrypted conversation, let’s consider UserX sitting in between User1 & User2, UserX will be able to capture all the communication between User1 and User2. As UserX sitting in the middle, he will be able to capture the secret key being shared between user1 & user2. After key is shared both the parties will start communication in encrypted mode without knowing that the userX is capturing their communication & as userX as already captured a secret key UserX is able to decrypt all the content transferred between User1 & User2.
Brute Force Attack:
Consider a scenario of the combination lock with two decimal digits, each has possibility of 0 to 9. If I want to open the lock without knowing the correct code, I may try all possible combination until I found the correct one; In this case of two digits combination lock, it may have maximum 100 possibilities (00 to 99). I may try all possibilities & get the correct combination code.
In Case attacker has capture ciphered data encrypted with 56bit DES algorithm, but don’t have secret key to decrypt it. What attacker can do is try all different possible keys. 56 bit key size may have 256 possibilities; Attacker may try all the possible key combination systematically until found the correct one. As key size increases, more key combination have to check by the attacker, which takes more time to crack the key. Please look at the following table of key length v/s brute force combinations from wikipedia.
Symmetric key length vs brute force combinations | ||
Keysize in bits | Permutations | Brute force time for a device checking 256 permutations per second |
8 | 28 | 0 milliseconds |
40 | 240 | 0.015 milliseconds |
56 | 256 | 1 second |
64 | 264 | 4 minutes 16 seconds |
128 | 2128 | 149,745,258,842,898 years |
256 | 2256 | 50,955,671,114,250,100,000,000,000,000,000,000,000,000,000,000,000,000 years |